Performance enhancement of TinyECC based on the multiplication optimizations
Hwajeong Seo,Howon Kim,Kyung-Ah Shim
|
Security and Communication Networks
6
(2013)
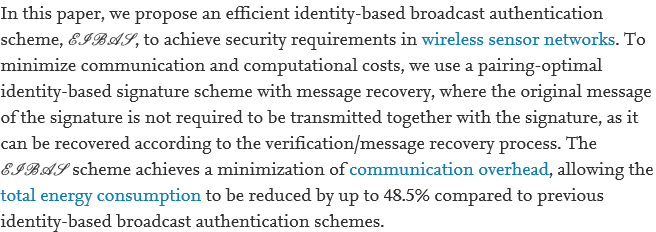
Because wireless sensor network (WSN), which is composed of a large number of lowcost and resourceconstrained devices, communicates on the basis of wireless protocols such as IEEE 802.15.4, ZigBee, and DASH7, it is easily vulnerable to eavesping, illegal modification, privacy infringement and denialofservice attacks. These attacks destroy the data integrity, confidentiality, and authentication of the basic WSN security requirements and then the reliability and security of the WSNbased applications are deteriorated. There have been many research efforts to make secure WSN environments. Among these efforts, TinyECC is one of outstanding works. It provides several security protocols such as Elliptic Curve Diffie–Hellman, Elliptic Curve Digital Signature Algorithm, and Elliptic Curve Integrated Encryption Scheme, based on the Elliptic Curve Cryptography (ECC). TinyECC is basically a wellwritten TinyOSbased code and is optimized to resourceconstrained environments. The Barrett reduction, hybrid multiplication, and several optimization techniques are also used for high performance even with lowenergy consumption. However, the hybrid multiplication technique used in TinyECC is known to be not suitable for 16bit processor, MSP430, which is a familiar processor for sensor node. This is due to the fact that the MSP 430 processor does not provide enough number of registers for hybrid multiplication techniques. Because the multiplication operation over the finite field is a major operation of the ECC, it causes a high latency of multiplication operations and eventually degrades the performance of the ECC operation. In this paper, we propose a novel multiplication operation based on the cached operands and reordered partial products. The proposed method shows that the latency of the polynomial multiplication, which is the core operation of the ECC, is 6% smaller than previously known results. Copyright © 2012 John Wiley & Sons, Ltd.
- 초록
Because wireless sensor network (WSN), which is composed of a large number of lowcost and resourceconstrained devices, communicates on the basis of wireless protocols such as IEEE 802.15.4, ZigBee, and DASH7, it is easily vulnerable to eavesping, illegal modification, privacy infringement and denialofservice attacks. These attacks destroy the data integrity, confidentiality, and authentication of the basic WSN security requirements and then the reliability and security of the WSNbased applications are deteriorated. There have been many research efforts to make secure WSN environments. Among these efforts, TinyECC is one of outstanding works. It provides several security protocols such as Elliptic Curve Diffie–Hellman, Elliptic Curve Digital Signature Algorithm, and Elliptic Curve Integrated Encryption Scheme, based on the Elliptic Curve Cryptography (ECC). TinyECC is basically a wellwritten TinyOSbased code and is optimized to resourceconstrained environments. The Barrett reduction, hybrid multiplication, and several optimization techniques are also used for high performance even with lowenergy consumption. However, the hybrid multiplication technique used in TinyECC is known to be not suitable for 16bit processor, MSP430, which is a familiar processor for sensor node. This is due to the fact that the MSP 430 processor does not provide enough number of registers for hybrid multiplication techniques. Because the multiplication operation over the finite field is a major operation of the ECC, it causes a high latency of multiplication operations and eventually degrades the performance of the ECC operation. In this paper, we propose a novel multiplication operation based on the cached operands and reordered partial products. The proposed method shows that the latency of the polynomial multiplication, which is the core operation of the ECC, is 6% smaller than previously known results. Copyright © 2012 John Wiley & Sons, Ltd.
- 초록
Because wireless sensor network (WSN), which is composed of a large number of lowcost and resourceconstrained devices, communicates on the basis of wireless protocols such as IEEE 802.15.4, ZigBee, and DASH7, it is easily vulnerable to eavesping, illegal modification, privacy infringement and denialofservice attacks. These attacks destroy the data integrity, confidentiality, and authentication of the basic WSN security requirements and then the reliability and security of the WSNbased applications are deteriorated. There have been many research efforts to make secure WSN environments. Among these efforts, TinyECC is one of outstanding works. It provides several security protocols such as Elliptic Curve Diffie–Hellman, Elliptic Curve Digital Signature Algorithm, and Elliptic Curve Integrated Encryption Scheme, based on the Elliptic Curve Cryptography (ECC). TinyECC is basically a wellwritten TinyOSbased code and is optimized to resourceconstrained environments. The Barrett reduction, hybrid multiplication, and several optimization techniques are also used for high performance even with lowenergy consumption. However, the hybrid multiplication technique used in TinyECC is known to be not suitable for 16bit processor, MSP430, which is a familiar processor for sensor node. This is due to the fact that the MSP 430 processor does not provide enough number of registers for hybrid multiplication techniques. Because the multiplication operation over the finite field is a major operation of the ECC, it causes a high latency of multiplication operations and eventually degrades the performance of the ECC operation. In this paper, we propose a novel multiplication operation based on the cached operands and reordered partial products. The proposed method shows that the latency of the polynomial multiplication, which is the core operation of the ECC, is 6% smaller than previously known results. Copyright © 2012 John Wiley & Sons, Ltd.
More