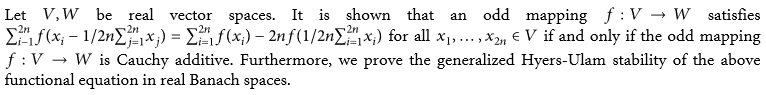논문
Security Analysis of Two Certificateless Signature Schemes
심경아, 이주희, 이향숙 | Journal of the Korea Institute of Information Security & Cryptology (정보보호학회논문지) 19/6 (2009)
Decomposition theorem on G-space
Taeyoung Choi and J.Kim | Osaka Journal of Mathematics 46-1 (2009)
Yeol Je Cho; Xiaolong Qin; Jung Im Kang | Nonlinear Analysis: Theory, Methods & Applications 71-9 (2009)
Strong convergence theorems for an infinite family of nonexpansive mapping in Banach spaces
X. Qin, Y. J. Cho, J. I. Kang, S. M. Kang, | Journal of Computational and Applied Mathematics 230-1 (2009)
Ghost matrices and a characterization of symmetric Sobolev bilinear forms
K. H. Kwon, L. L. Littlejohn, and Gang Joon. Yoon | Linear Algebra and its Applications 431-1~2 (2009)
Convergence of a fixed point iteration method for OSV model
Dokkyun Yi, Do-Hyung Kim, Eunyoun Kim, Sung-Dae Yang | Applied Mathematics and Computation 215-5 (2009)
Qusrdratic functional equations associated with Borel functions and module actions
Park, Won-Gil; Bae, Jae-Hyeong | Bulletin of the Korean Mathematical Society (대한수학회보) 46-3 (2009)
Functional equations related to inner product spaces
Choonkil Park, Won-Gil Park, and Abbas Najati | Abstract and Applied Analysis 2009-Article ID 907121 (2009)
Six-state clock model on the square lattice: Fisher zero approach with Wang-Landau sampling
Chi-Ok Hwang | Physical Review E 80 (2009)
J.H. Yoo; C.-O. Hwang; T. Won | Molecular Simulation 35-9 (2009)